We Will Help Evolve your Capabilities to Make Your Transformations and Your Enterprise- Secure
Copyright © 2024 Trianz
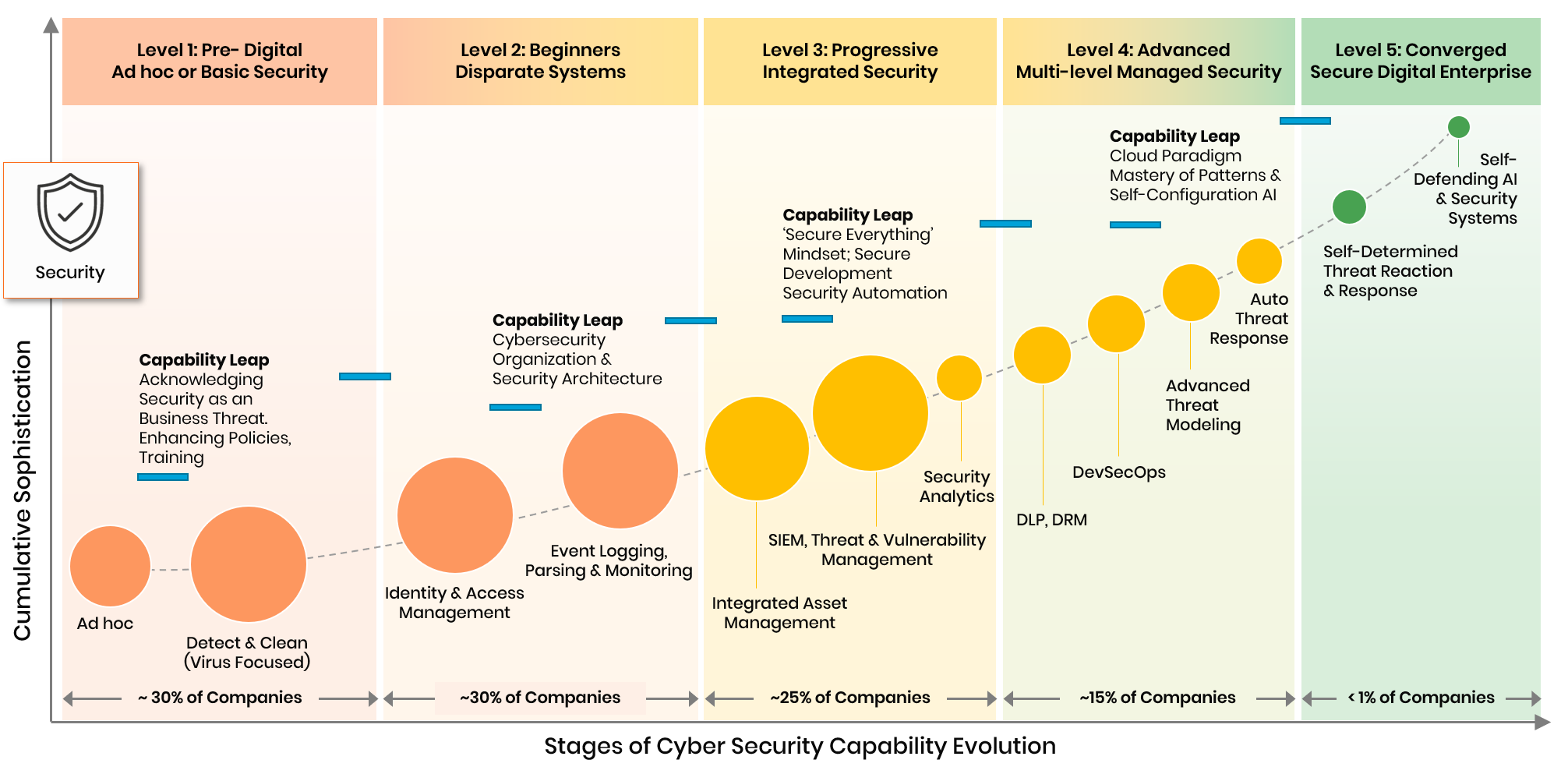
Of all the technology pillars that combine to propel digital transformations forward, Security is the most complex, invisible and yet essential for success. Our data shows that cybercrime is accelerating at nearly 2X of digital transformation and so without security, there will be no digital transformations.
Historically, cyber security events such as hacking, IP theft, financial theft and even ransoms were successfully kept under the wraps. Recent events have proven otherwise with criminals getting their goods while ensuring maximum adverse publicity. Cyber security attacks are no longer of financial consequence alone but they affect the brand image of a company and the trust various stakeholders place in it.
Spectacular events aside- our data shows that nearly 70% of breaches are unnoticed and therefore unreported. That is because 60%+ companies do not develop comprehensive threat perceptions and evaluations and are completely unprepared for such attacks. By the time, it happens- it is too late.
Finally- the cost and damage to customers of any company- the ultimate stakeholders to nations as a whole from loss of IP and secrets is so large that it is a matter of time before we see major security regulations.