As businesses increasingly adopt cloud technology to stay competitive, they also need to have safe and secure systems to keep their businesses intact. Cloud security offers significant benefits to businesses through automated systems that provide 24/7 continuous protection, without the need of human intervention.
The potential risks that businesses face include:
- Lack of security systems resulting in downtime in the event of an attack, leading to productivity loss
- DoS and DDoS attacks leading to outage or service disruption
- Lack of well-rounded cloud security systems lead to regulatory compliance challenges
Cloud security systems enable automation which can protect a business from losses caused due to breaches. Robust services also include management of data protection compliance issues and disaster recovery.
The Benefits of a Cloud Security System
Automation
Reduced reliance on human intervention which in turn results in less room for error.
Agility
Improve data security and regulatory compliance through timely patching, and updates decreasing downtime.
Safety
Real-time alerts on threats help protect against external and internal sources.
Proactive
Security embedded into the system enabling proactive response to threat.
Enhance Enterprise Infra Security with Concierto
Ensure robust security protocols and protect your cloud assets with Concierto Multi-Cloud Management Platform.

What is a Managed Cloud Security Service?
A Cloud Security Managed Service is a type of cloud management provision that offloads security monitoring, reporting, and technical support to an external provider. It can include managing intrusion detection, firewall management, oversight of the company's virtual private network (VPN), anti-virus configuration and vulnerability testing.
Employing managed security services means that internal IT teams have more time to focus on new business developments, while an outside expert team manages all aspects of cloud cybersecurity for your company.
Some companies, however, are concerned with information confidentiality and may be hesitant to outsource their valuable data. But setting up an in-house security operations center can be more expensive and less secure than partnering with a managed cloud security services provider. Cost considerations include:
Staffing
Software licensing
Hardware
Implementation costs
Management costs
While there are some key scenarios where an in-house security operations center is optimal, for most companies the disadvantages outweigh the advantages. A managed security service provider is staffed with a team of professionals who are experienced in a range of security issues and can be counted on to resolve the problem quickly.
Whomever you choose to work with, take the time needed to ensure that service level agreements meet your needs now and going forward as you scale, the provider is accredited with key cloud platform partnerships, and that you trust them with your sensitive data.
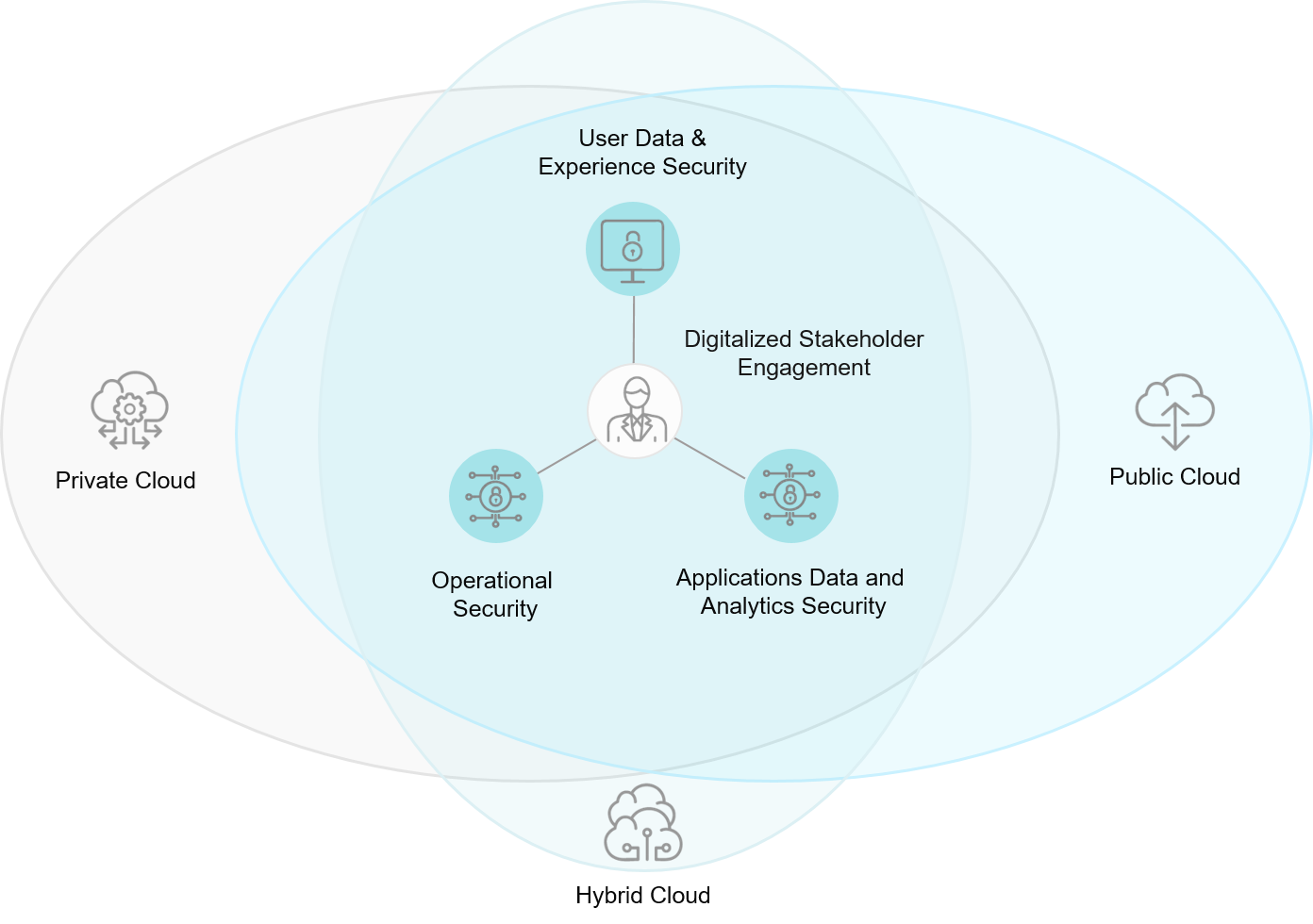
Cloud Cybersecurity Challenges
Threats aside, these days there are numerous new challenges that require significant expertise to ensure compliance with cloud security best practices. The challenges include:
- Security compliance is incredibly important in the cloud, with regulations such as HIPAA, GDPR, and PCI-DSS offering a framework for network security. Your team may not have the current training or expertise to fully comply with these regulations, resulting in sanctions if protocol is improperly followed.
- Multi-cloud expertise environments require significant administration and development expertise within the Azure and AWS ecosystems. To cultivate this expertise in-house, companies must invest heavily in staff development.
- Traditional security solutions operate differently from ones in the cloud. For the uninitiated, the cloud's automatic scan reporting could cause alarm due to false positives.
On the flipside, without the right skillset, your staff could compromise your network security by misconfiguring it. Because the cloud allows you to automate security actions, a malicious file could be incorrectly flagged as safe without careful management, exposing your network to attackers.
Our research shows that only 7% of companies are digital champions, meaning they have succeeded in their digital transformations. 60% of digital champions use proactive and predictive security systems, indicating a higher level of maturity by using integration for maximizing speed and efficacy.
Trianz has invested in creating one of the world's largest databases on digital transformations with data from over 5,000 companies spanning 20 industries.
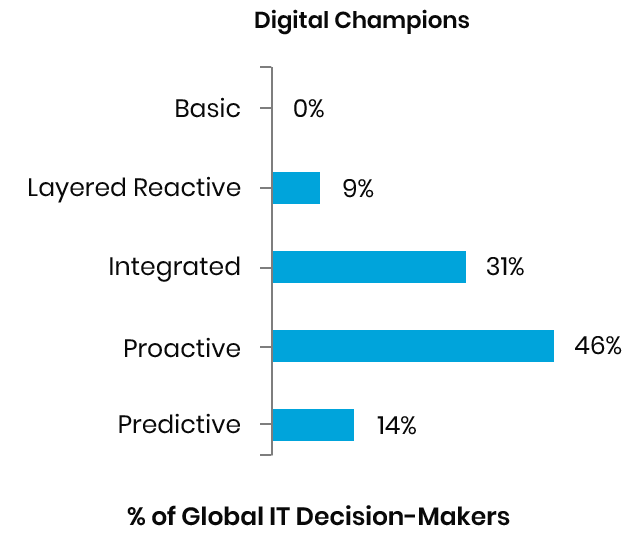
Mastering Cloud Security
When searching for a consulting partner that offers comprehensive cloud security managed services to its clients, look for one with decades of experience in the IT industry, and pay particular attention to the following attributes:
Scalability
Expert consultants leverage the functionality present in leading cloud security tools, allowing for the automation of incident reports and scaling of SecOps as your cloud network expands.
Agility
Look for deep working knowledge of security industry best-practices and cloud adoption frameworks, essential for tailoring a curated managed security plan suited to your business needs. Also, a cloud-agnostic approach ensures the vendor can offer managed security services across all popular public cloud platforms.
Flexibility
The right vendor will support the use of open-source tools and allow you to bring your proprietary tools to the cloud. Existing software licenses can be easily transferred, saving you money on your new managed services package.
Effective
The use of powerful SecOps tools can generate a bird's eye view of your network, enabling comprehensive security management for your business. At every point throughout the consultation, you will need routine, acute analysis and recommendations that fit into your existing IT strategy.
Compliant
Adherence to security regulations can help you protect your data and avoid hefty fines. Look for a vendor with expertise in the General Data Protection Regulation (GDPR), Health Insurance Portability and Protection Act (HIPAA), National Institute for Standards and Technology (NIST), and Payment Card Industry Data Security Standard (PCI-DSS).
Case Study: AWS Cloud Managed Services for Financial Services Provider
Bottom line, your managed cloud security services provider should be a partner in building a business process where security is an integral part of the development process, allowing for vulnerability detection at an early stage and cost-savings before it turns into a problem. A security posture that includes continuous audits and assessments will positively impact enterprise value and foster a culture of security within the organization.
The Trianz Difference
Trianz is a leading IT services and consultancy firm with more than a decade of experience helping businesses improve their IT services. Our Cloud Security Managed Services are among the best in the industry, thanks to regular third-party security audits that certify us in SOC-1, SOC-2, ISO 27001, and PCI-DSS implementation.
Powered by knowledge, research, and perspectives, we enable clients to transform their business ecosystems and achieve superior performance by leveraging infrastructure, cloud, analytics, digital, and security paradigms. Reach out to get in touch or learn more.


