What is AWS IoT?
AWS IoT provides cloud services that can connect billions of devices and trillions of messages that are securely routed between any given AWS endpoint. The Amazon Web Services IoT Platform includes features already standard to base AWS, such as Amazon Kinesis, Amazon S3, Amazon DynamoDB, Amazon CloudWatch, and AWS CloudTrail.
Employing IoT technology decentralizes administration and allows you to use any internet-enabled device around the world to access these features.
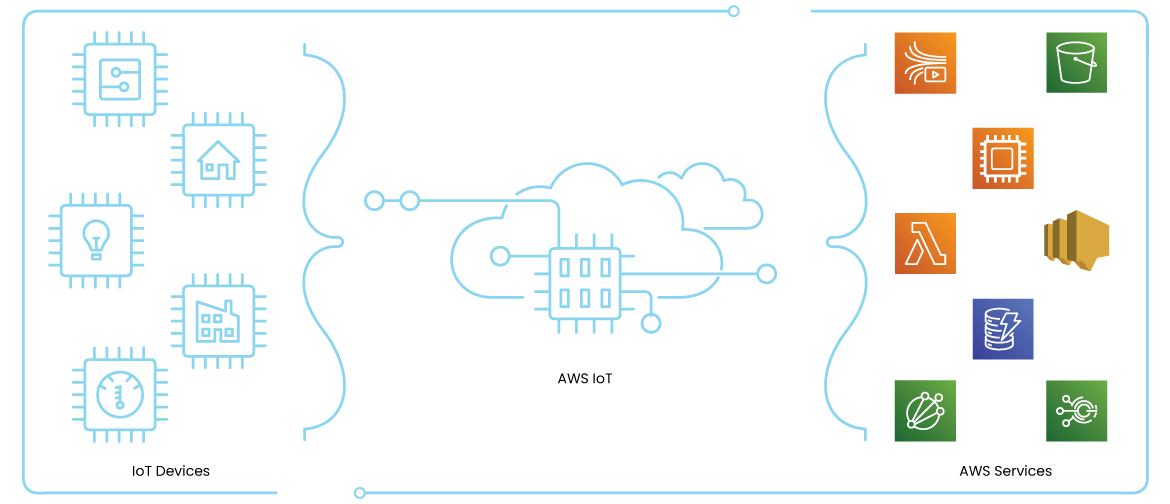
How Do You Use AWS IoT?
Amazon makes IoT configuration simple. Users simply sign into the IoT web console, register, configure your devices, test parameters you create for the devices, and then create and track IoT-relevant jobs. There are numerous articles you can find on the AWS website that offer detailed tutorials and walkthroughs on their products and services.
A newer feature introduced into the AWS IoT ecosystem involves integrating machine learning to create a framework for automated models to complete tasks more quickly and efficiently.
For instance, by collecting real-time data from IoT devices using Amazon SageMaker, a business can use an AI engine to automate the information processing and connect multiple data sources to contextualize the information for the end user. The machine can then provide a personalized response or experience directly to the end user, or route the response back to automate another process that will help troubleshoot the issue.
To accommodate any industry or business, Amazon offers tiers of membership depending on your skill level with their products and your business needs. If you are just looking to explore and play around, users are welcome start with a free limited trial. Need to support thousands of devices and a multitude of tool? AWS IOT also makes it simple to manage your fleets of connected devices at any scale.
Also Read: ECS vs. EC2
Security on AWS IoT
AWS IoT Security implements modern and secure measures such as two-factor authentication and end-to-end encryption to prevent malicious users from accessing sensitive information. Granularity is also key with AWS IoT. Group policy makers can configure devices with the strictest set of rules to manage how users interact with data and the AWS client interface.
Examples of basic parameters might include mandatory 30-day password changes, file permissions, and even scheduled system lockdowns coupled with more advanced features.
Today, the different manifestations of AWS IoT devices are limited only by your imagination. We have smart fridges, smartwatches, internet-enabled lighting, and home security systems, with more clever and functional innovations popping up every day. Leaders like Apple, Amazon, Microsoft, along with a massive slew of startups, compete in this space to bring you the very best in smart products without sacrificing form over function.

AWS IoT Security Best Practices
IoT services as a platform empowers users with many security measures to protect the enterprise. Some of the best practices within these security measures include:
Creating your unique business identity on their platform
Protecting that identity with authentication and authorization measures
Employing public and private key mechanisms
Using policy variables in authorization policies
Using security certificates as an additional step
Each time a user interacts with the AWS console, one or all of these measures could be engaged. Your employee could authenticate their identity with either the company ID or their unique sign-in credentials, at which point they may only be authorized to do certain tasks once logged in.
Certificates ensure AWS that you are whom you say you are. Certificates are like a signature that is unique to an authorized person. By provisioning a certificate to each of your devices, if a particular device’s credentials were compromised only that device would be impacted. The certificate can then be revoked so as not to compromise the entire system.
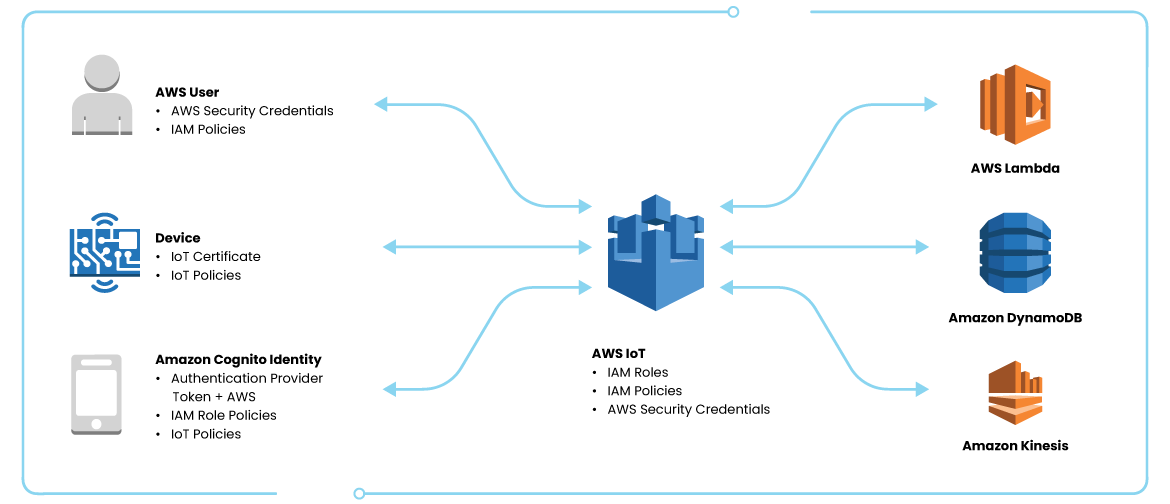
With AWS IoT Device Defender, users are empowered with a fully managed auditing service. Device Defender audits IOT resources associated with your devices (e.g., X.509 certificates and IoT policies) to ensure they are not deviating from best practices, and will send alerts if any gaps indicate a security risk. These alerts provide contextual information and recommendations to investigate and mitigate the issue.
In addition, AWS IoT Device Defender continuously monitors security metrics from the cloud and user devices against defined rules to identify unexpected behavior that may indicate a compromised device. With AWS IoT Device Defender you can:
Receive alerts to unusual behavior
Maintain a secure cloud IoT
Configuration monitor device behavior
Get better insight into the sources of threats
How Trianz Can Help You With AWS IoT Implementation
As an Advanced Consulting Partner and Managed Service Provider for AWS, you can trust that Trianz will take the best practices of AWS IoT and put them to their greatest use for your business. If you do not already employ mobile or smart technology in your workplace, Trianz consultants will help with the transition to provide your company with the full benefit of elasticity in the AWS cloud.
Remember, AWS IoT means options and a greater increase in data gathering. With this new assortment of devices at your disposal you can collect Big Data you may not have even known was out there. No matter what business or industry you are in, our experts can reveal data monetization opportunities for you, propelling your organization into more insightful use of data.











