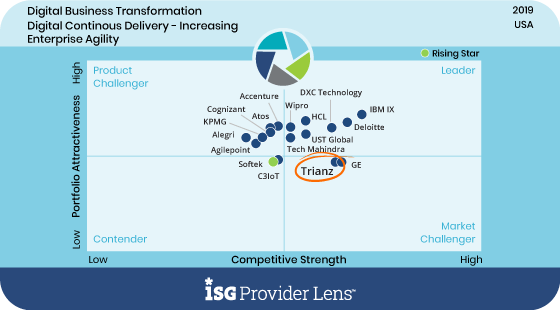
Preventing Security Risks
Cloud adoption has grown tremendously – some 83% of enterprise workloads and 94% of enterprises use cloud services. As we have seen so frequently in the news, this growth brings with it a significant increase in cyberattack risks.
Security must be proactive and hyper-vigilant to ensure a safe, incident-free business environment for all stakeholders – i.e., regulators, customers, partners, suppliers, leadership, and employees. By taking action to secure your data on the cloud, you can avoid threats such as:
Insecure APIs and interfaces
Misconfigurations and account hijacking risks
Data breaches resulting in compliance challenges
Identity access management issues and privilege creep risks
Inadequate logging and monitoring

Cloud Security Assessment
To achieve security in the cloud, the first step for your organization is conducting a cloud security assessment to determine your enterprise’s cloud security posture. We will work with you to create an assessment that helps you understand your current state, gaps, and intended future state.
A thorough cloud security assessment will also provide actionable insights about misconfigurations and other departures from cloud security recommendations, empowering organizations to uncover, curb, and recover from unwelcome incidents. It is critical to invest in security assessments and strategies to maximize the value of cloud computing.
Cloud Security Strategy
While undergoing a cloud migration, you have an excellent opportunity to build a secure IT foundation for your business. A cloud security strategy can also be executed in enterprises already in the cloud, further strengthening their existing network.
Trianz’ seasoned experts in cloud security strategy deliver best-in-class recommendations for:
Data privacy and encryption in the cloud
In-depth defense with DLP, PAM, anti-malware, and ransomware protection tools
Self-determined threat reaction and response
Security analytics
Self-defending, AI-enabled security systems
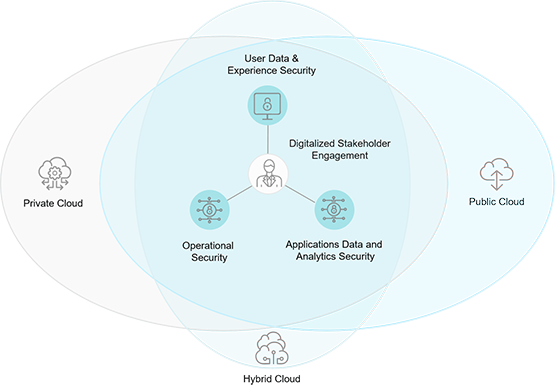
Model of a Cloud Security Ecosystem
Copyright © 2022 Trianz